ZK-STARKs: Scalable, Transparent Proofs Architecting a More Secure Web3
Body
A New Era of Blockchain Verification
Nowadays the requirements that are imposed on blockchain networks are no longer limited to decentralization or immutability. Users, developers and institutions are now in need of systems that are capable of scaling effectively and maintaining security and privacy. The first blockchain designs had serious drawbacks: they were costly to run, sluggish, and sensitive data were revealed. These limitations brought out the necessity of a novel generation of cryptographic solutions that are fast, transparent and scalable. A new technology known as ZK-STARKs has revolutionized the currently used innovations, which allow blockchain systems to authenticate intricate tasks without losing privacy or network integrity.
Web3 has increased these requirements. With the growth of applications to not only financial transactions but to decentralized identity, gaming, AI computations, and high-security data sharing, the traditional verification methods are finding it difficult to keep up. ZK-STARKs offer a decently fast, transparent, and secure solution that enables networks to work at scale without overloading nodes and revealing confidential information.
The transformations of the ZK-STARKs on verification
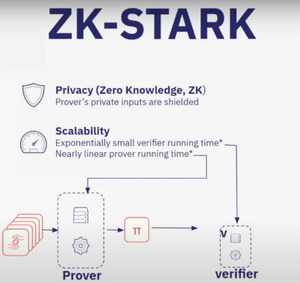
The ZK-STARKs (which is known as Zero-Knowledge Scalable Transparent Argument of Knowledge) reinvent the possibilities of blockchain validation. As opposed to previous zero-knowledge structures that were based on a trusted setup, ZK-STARKs are completely transparent, which removes the threat of undermined parameters. They enable a prover to prove the validity of computations regardless of any underlying information, and the resulting proofs can be proved by anyone with little computation.
Scalability is the main benefit of ZK-STARKs. Compressing large batches of transactions or complicated computations into a single proof can reduce the processing requirements in the on-chain to a drastic scale. Such compression not only speeds up the process of transaction validation but also reduces fees and energy consumption by a large margin. Practically, ZK-STARKs offer both the performance and throughput needed to support high-performance blockchain systems and the security assurances needed in trustless systems.
Quantum resistance is also another essential characteristic. ZK-STARKs are resistant to possible quantum attacks because they use the hash-based cryptography over elliptic curves, so blockchain verification is secure even with the improvement of computation power.
ZK-STARKs in Practice
ZK-STARKs effects are felt in various fields of Web3. When it comes to layer-2 scaling, these proofs can be used to construct rollups, which combine thousands of transactions into a single proof, decreasing the usage of the main chain and without losing verifiable accuracy. Stark Net and other networks are using this method to offer more scalable, cheaper and faster decentralized application transactions.
Another field where ZK-STARKs have changed is privacy-preserving computation. Finance, healthcare, and AI are examples of industries that can run sensitive calculations off-chain and validate their correctness on-chain to ensure compliance without loss of confidential data. Citizens are able to engage in intricate digital ecosystems without sharing personal or business-sensitive data.
It is also advantageous to decentralized identity systems. With the help of ZK-STARKs, one is able to validate their age, citizenship or certification without showing the personal information behind. Such a biased disclosure strategy compromises privacy with checking, permitting safe communications in regulatory and sensitive settings.
The tangible improvements are also being witnessed even in gaming and high-throughput dApps. Complex game logic or those processes that are computationally intensive can be implemented by developers without affecting the user experience or congesting the main chain. Applications can perform a level of computation and security that was previously not possible with standard on-chain computations through the use of ZK-STARKs.
The Wider Implications of Web3
The implementation of ZK-STARKs marks the change in the structure of blockchain infrastructure. Networks are now capable of more activity, more complicated calculations, and privacy, without compromising trust or decentralization.
This ability changes the adoption and integration calculus as an investor and developer. Scalability or privacy-related projects that felt reluctant to use blockchain have been solved. Organizations are able to run sensitive workloads on-chain without revealing their proprietary data, and regulators can ensure that work is correct without requesting raw information.
Moreover, ZK-STARKs are able to create confidence among users and participants due to their transparency and security. Checking is mathematically assured and it eliminates the use of intermediaries or opaque checks. Such a combination of efficiency, privacy, and auditability is the basis of a Web3 ecosystem that is set to support mass adoption, complex applications, and high-security settings.
Conclusion
ZK-STARKs mark the next stage of development of blockchain technology. They allow networks to run efficiently and without undermining security or privacy by allowing scalable, transparent and quantum resistant proofs. Regardless of using layer-2 scaling, privacy-preserving computations, decentralized identity systems, or high-performance dApps, ZK-STARKs offer a platform upon which the next generation of secure, high-performance, and trustful blockchain systems can be built.
With the further expansion and usage of Web3, the inclusion of ZK-STARKs will probably become a mandatory condition instead of a bonus feature. They offer the mathematical certainty, scalability and secrecy that networks require to sustain advanced applications, meet regulatory anticipations and offer a user experience that fulfils the need of an ever more digitalized world. ZK-STARKs can only be described in this light as not only a technological advancement but also the pillar of a more secure, efficient, and transparent Web3 ecosystem.







Comments